2024-2-19 18:46:43 Author: cyble.com(查看原文) 阅读量:33 收藏
Key Takeaways
- A recent discovery revealed a new version of the CriminalMW Android Banking Trojan, which is being advertised for rent at a rate of $5000 per month on their Telegram channel.
- The latest updates to the CriminalMW (Criminal Malware) include the implementation of new commands, a new overlay technique, the creation of Google Play Store phishing websites, and the integration of additional features.
- This updated version of CriminalMW specifically targets 10 Brazilian banks through the PIX platform, leveraging an Automated Transfer System (ATS) Framework.
- Apart from SickoDevZ, three other Threat Actors (TAs) identified — “Flyn”, “Malino”, and “Pereira” have been linked to the malware. Their involvement was confirmed through their Telegram handles and references to the CriminalMW.
- During a recent operation, the Federal Police arrested individuals suspected of involvement in the Grandoreiro Banking Trojan case. The São Paulo Police also arrested SickoDevZ. This arrest has led to suspicions regarding SickoDevZ’s potential connection to or involvement in the aforementioned case.
- Furthermore, a new rebranding effort known as WebDroid has been uncovered, indicating ongoing development and evolution within the CriminalMW Group, despite the aforementioned arrest, indicating a broader network at play.
Overview
In 2023, Brazil experienced a notable increase in sophisticated Android threats targeting financial institutions, with a particular focus on the PIX platform, an innovative instant payment system. The majority of these Android malware variants were developed by a Brazilian developer known as “SickoDevZ” with an Automatic Transfer System (ATS) implementation to target banks and execute fraudulent transactions on a large scale.
GoatRAT, FantasyMW, and CriminalMW (Criminal Bot) emerged in 2023, all linked to the developer SickoDevZ. Besides SickoDevZ, three other threat actors, “Flyn“, “Malino“, and “Pereira,” were also identified in connection with this malware. During our investigation, we were able to identify the Telegram handle of Threat Actor “Pereira” and “Malino”, mentioning the Criminal Malware Group in the profile along with CriminalMW’s public Telegram channel.

Figure 1 – Telegram Handle of Threat Actor Pereira

Figure 2 – Telegram handle of Threat Actor Malino
In addition to these two handles, the threat actors behind the CriminalMW were operating a Telegram community channel, where they were observed advertising the rental of Criminal Malware for $5000 per month.

Figure 3 – CriminalMW rental advertisement on the community Telegram channel

Figure 4 – Translated Rental advertisement of CriminalMW
On February 1, 2024, the threat actor deleted the chat and pinned messages from the public Telegram channel of the “Criminal Malware Group” and subsequently renamed it to “SAI POR SEGURANÇA” (which translates to “LEAVE FOR SAFETY”).

Figure 5 – Deleted chat and pinned message from public Telegram channel
During our investigation, we were able to access archived messages from the Telegram channel via an analytics site. This enabled us to recover deleted messages from February 1, 2024, shedding light on the reason behind removing messages. According to a recent post in the Telegram archive, the threat actor was informing users/subscribers about an operation, and SickoDevZ had fled. Consequently, the CriminalMW project would be suspended until a solution was found.

Figure 6 – Archive post from the Telegram channel about the operation
According to reports from Brazilian news publications, the São Paulo Police arrested an 18-year-old couple suspected of involvement in a banking scam, which featured the CriminalMW website in their news coverage.
While this news can indicate that the TA, SickoDevz, may have been arrested, the posts on their Telegram channel (Figure 6) suggest that they may have evaded capture and are still at large.
Additionally, during the same period, the Federal Police made arrests in São Paulo and other regions of Brazil in connection with the Grandoreiro Banking Trojan case on January 30, 2024. The swift deletion of posts and SickoDevZ’s departure following these arrests raised suspicions that they could be involved or suspected of involvement in the same case.
Despite the deletion of the primary Criminal malware group Telegram channel, the community channel continues to operate, where “Malino” is observed actively engaging in discussions and addressing community queries. Their discussions revealed that they had restricted access to their tool, releasing them exclusively to existing customers.

Figure 7 – Community conversation related to the status of CriminalMW malware
An Analysis of the CriminalMW Group’s Rebranding Tactics
In March 2023, Cyble Research and Intelligence Labs (CRIL) identified GoatRAT, a Banking Trojan utilizing ATS to target Brazilian banks. Following the discovery of GoatRAT, SickoDevZ rebranded the malware as “FantasyMW” and then “CriminalBot (CriminalMW)” later in 2023. More recently, a new variant named “WebDroid” has emerged, suspected to be another iteration of GoatRAT. The following timeline outlines the sequence of malware rebrands associated with the CriminalMW group.

Figure 8 – Timeline of SickoDevZ’s malware rebrand and updates
GoatRAT (March 2023)
GoatRAT was identified as being distributed through a shortened URL in March 2023. This variant of GoatRAT focused on targeting three banks using the ATS method, concealing its malicious operations through an overlay screen. The malware established communication with the Command and Control (C&C) server at hxxp://api.goatrat[.]com, while its admin panel was hosted on the URL hxxp://goatrat[.]com.

Figure 9 – Admin panel of GoatRAT malware
During the discovery of this malware, SickoDevZ was actively utilizing a Telegram channel, where he identified himself as the owner of the GoatRAT malware. However, it has been observed that the Telegram channel has been inactive after his arrest, and the description mentioning the GoatRAT malware has been removed from the profile.
FantasyMW (April 2023)
In April 2023, the researcher identified FantasyMW as a rebrand of GoatRAT, which was available for rent at $5000. It becomes apparent that the rebranded malware was created by the same developer when the admin panel’s username is highlighted as “SickoDevZ”, and an image featuring the developer’s name was discovered within the APK’s resources.

Figure 10 – SickoDevZ overlay image present in FantasyMW APK file
After the initial discovery of FantasyMW, multiple iterations of the malware were observed. In contrast to GoatRAT, FantasyMW expanded its range of targets. The last updated version of the Fantasy malware, in particular, focused on 8 banks in Brazil and included additional code designed to counter emulation techniques.
CriminalMW (July 2023)
In July 2023, CRIL identified the rebranded variant of the GoatRAT malware known as “CriminalMW,” with its admin panel hosted at the URL “hxxps://bananasplit[.]shop.” This malware variant closely resembled the updated iteration of FantasyMW, employing a third-party library for anti-emulation techniques and employing the ATS. Notably, the admin panels of CriminalMW and FantasyMW shared identical user interfaces.

Figure 11 – Criminal Bot Admin Panel
Following the rebranding of the malware from FantasyMW to CriminalMW, CRIL uncovered a new URL associated with CriminalMW, “hxxp://criminalmw[.]fun.” This URL serves as a platform for advertising CriminalMW, offering comprehensive information about the malware itself and additional details concerning the CriminalMW team.

Figure 12 – CriminalMW website

Figure 13 – CriminalMW panel
During our investigation of the CriminalMW URL, we noticed the presence of the following subdomains linked to the CriminalMW:
- cmw.criminalmw[.]fun
- spartan.criminalmw[.]fun
- customersapi.criminalmw[.]fun
- hvnc.criminalmw[.]fun
- api.criminalmw[.]fun
- apix.criminalmw[.]fun
- clientes[.]criminalmw.fun
Additional enhancements to the CriminalMW include the integration of HVNC (Hidden Virtual Network Computing) utilizing the Janus WebRTC library. Through this implementation, threat actors can interact with infected devices via the HVNC feature, using the VNC web panel hosted at “hxxps://hvnc.criminal[.]fun”.

Figure 14 – VNC web panel of CriminalMW
Upon analyzing the VNC-implemented sample (b2c99c8268764aa12f1a838e784360e48d9e6ad805b2927eec3d128a93ba3bb1), we observed a significant shift in the malware’s behavior, whereby it now operates based on commands received from the server. Unlike older samples of GoatRAT and FantasyMW, which were limited to implementing the ATS framework, the latest malware iterations exhibit an expansion in functionality.
Previously, samples identified in 2023 relied solely on the Accessibility Service to execute the ATS framework. However, recent malware samples are utilizing a broader set of permissions and introducing new features related to SMS and CALL_PHONE permission. Further details regarding these updates are discussed comprehensively in the technical analysis section.
Furthermore, we noticed that the CriminalMW group is offering an additional feature called “Page Generator,” which allows users to create Google Play Store phishing pages for the distribution of malware.

Figure 15 – Google Play Store phishing page generator feature
Despite the latest website of the CriminalMW being non-operational since February 01, 2024, our investigation has unveiled yet another rebranding effort orchestrated by SickoDevZ.
WebDroid – A Possible Rebrand From CriminalMW group
While investigating the CriminalMW, CRIL identified a website “hxxps://droidweb[.]net/” related to WebDroid. This website seemed to function as an admin panel, with no further details available.

Figure 16 – Web panel for WebDroid
Similar to the criminalmw[.]fun domain utilized by the CriminalMW, Webdroid also featured the following subdomains:
- vnc.droidweb.net
- api.droidweb.net
The vnc.droidweb[.]net subdomain hosted a VNC panel highly reminiscent of the HVNC panel found in the CriminalMW. Additionally, we observed that the CriminalMW URL is associated with the “About” field on the Webdroid VNC Panel, while the purchase and support sections are linked to the Webdroid VNC panel URL itself. These findings suggest that WebDroid is affiliated with the CriminalMW Group and undergoing a rebranding process, as evidenced by the missing URLs.

Figure 17 – VNC web panel for DroidWeb
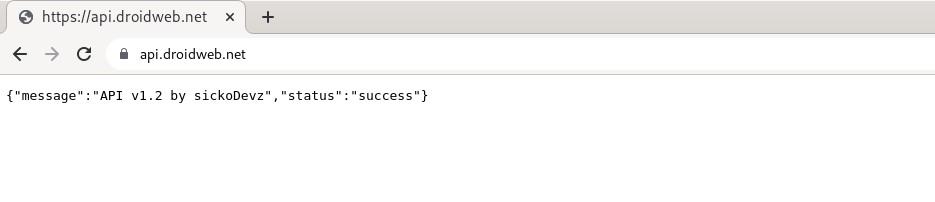
Furthermore, the subdomain “api.droidweb.net” displays a message regarding API v1.2 developed by SickoDevZ, as depicted in the figure below.

Figure 18 – Webdroid’s API URL developed by SickoDevZ
The domain droidweb[.]net was registered recently in November 2023, coinciding with our investigation, suggesting that SickoDevZ has initiated the development of a new rebranded version of their malware. We did not come across any malware samples linked to WebDroid through this analysis, however. However, the arrests, cessation of malware development, and disruption in the CriminalMW community increase the likelihood that the threat actor may rebrand the malware once again and begin distributing it in the wild under a new name.
As we explore the rebranding of malware from the CriminalMW group, we can speculate on the motivations behind this strategy. It’s possible they are rebranding to avoid detection by altering their code, to enhance market appeal and generate profits, or to experiment with new distribution channels to determine the most effective tactics for their operations.
The following section describes the technical analysis of the most recent sample of the CriminalMW, identified by the hash value “152b3cda192f092160c2f4eaa6d696d20f63cf27e3b479328d2f392891dce87a”, featuring upgraded functionalities made in January 2023. The recently identified samples contain the references of SickoDevZ and CriminalMW, as shown in the figure below.

Figure 19 – References of SickoDevZ and CriminalMW in recent samples
Technical Analysis
APK Metadata Information
- App Name: Calculadora
- Package Name: biz.uea.xgn
- SHA256 Hash: 152b3cda192f092160c2f4eaa6d696d20f63cf27e3b479328d2f392891dce87a

Figure 20 – Application metadata information
As previously discussed, earlier rebranded versions relied on a limited set of permissions due to their dependence on the ATS framework. However, as SickoDevZ began upgrading this malware, recent samples mentioned a broader range of permissions listed in the manifest file, which are subsequently exploited by the malware.

Figure 21 – Permissions mentioned in the older samples

Figure 22 – Permissions mentioned in the recent samples
Anti-emulation Technique
Previously, SickoDevZ was observed employing the rootbeer library to detect root access and implementing custom code for emulator detection. However, in the latest iteration of the CriminalMW, SickoDevZ has adopted another open-source project, “Android emulator detector” by mamykin-andrey, for emulator detection.

Figure 23 – Emulator detection code
Websocket Connection
After the malware successfully verifies anti-emulation checks, it proceeds to establish a socket connection to receive commands from the server.

Figure 24 – WebSocket connection
Below is the list of commands CriminalMW can receive:
| Command | Description |
| UPDATEPIX | Receives updated PIX key |
| SHOWMSG | Displays Toast message |
| CALL | Makes a Call on the number received from the server |
| PUSH | Creates PUSH notification |
| OPEN | Opens application |
| SENDSMS | Sends SMS from the infected device |
| FORCEACESSIBILITY | Prompts to grant Accessibility service |
| FORCESBPS | Prompts to grant overlay permission |
| REMOVEOVERLAYS | Removes overlay |
| ATIVARSILENTY | Enables silent mode |
| DESATIVARSILENTY | Disables silent mode |
| OCULTARAPP | Hides application icon |
| EXIBIRAPP | Makes application icon visible |
| KILLBOT | Uninstall itself |
| Connected | Collects installed application |
Receiving PIX Keys
While establishing the socket connection, the malware simultaneously connects to the Pastebin URL to retrieve the PIX key belonging to the threat actor. Below are the URL and the PIX key used in the recent samples.
| URL | PIX Key |
| hxxp://pastebin.com/raw/SJy4nR8P | [email protected] |
| hxxp://pastebin.com/raw/wMfzBAB9 | [email protected] |
| hxxp://rentry.co/x8rh3/raw | [email protected] |
| hxxp://pastebin.com/raw/mkEvwaaX | [email protected] |
| hxxp://pastebin.com/raw/uBbAc6hn | [email protected] |
| hxxp://pastebin.com/raw/EikLKKhR | 07919731585 |
The presence of the Threat Actor’s names within the PIX keys “[email protected]” and “[email protected]” suggests that these two PIX keys belong to the CriminalWM Group.
ATS Framework
The implementation of the ATS Framework has remained consistently uniform across all rebranded versions of the malware. In contrast, we observed that one additional check has been implemented in the ATS framework to verify whether the device is in silent mode. This check may have been introduced by SickoDevZ to facilitate the money transfer process without disruption and to minimize arousing suspicion among victims. The steps involved in implementing the ATS framework are as follows:
- Check the target application’s package name
- Prompts for the Overlay permission, if not enabled
- Verifies if the device is on silent mode (Silent mode is operated on server command)
- Hides ATS activity with an overlay
- Execute ATS to transfer money received from the Pastebin URL
- Removes overlay
In older samples, the overlay image was kept in the resource folder of the APK file. However, SickoDevZ has now shifted to creating overlays using HTML code and incorporating GIF images sourced from legitimate banks’ websites, as depicted in the figure below:

Figure 25 – Creating overlay using HTML code and leveraging gif image from legitimate bank website
The full list of targeted banking applications is given below:
| Package name | Application name |
| br.com.bb.android | Banco do Brasil: abrir conta |
| br.com.gabba.Caixa | CAIXA |
| com.picpay | PicPay: cartão, conta e pix |
| com.mercadopago.wallet | Mercado Pago: cuenta digital |
| com.bradesco | Bradesco: Conta, Cartão e Pix! |
| com.itau.iti | iti: banco digital, cartão e + |
| com.c6bank.app | C6 Bank: Cartão, Conta e Mais! |
| com.recarga.recarga | Pix Parcelado Cartão Crédito |
| br.com.uol.ps.myaccount | PagBank Banco, Cartão e Conta |
| br.com.intermedium | Inter&Co: Conta, Cartão e Pix |
A comprehensive description of the ATS attack can be found in our blog post about the GoatRAT Android Banking Trojan.
Conclusion
The surge in sophisticated Android malware targeting financial institutions, particularly in Brazil and focusing on the innovative PIX platform, presents a significant threat to both users and financial systems.
Originally designed to streamline instant payments, the PIX platform has become a prime target for threat actors like SickoDevZ, who exploit its capabilities for financial fraud. The progression of malware variants, spanning from GoatRAT to FantasyMW, CriminalMW, and potentially WebDroid, underscores the adaptability and determination of these threat actors in leveraging technology for illicit purposes.
Despite the intervention of law enforcement and the arrest of SickoDevZ, the distribution of the CriminalMW remains active, suggesting a potential rebranding effort from the CriminalMW Group. Additionally, we suspect that following SickoDevZ’s inactivity, the CriminalMW group may recruit a new developer, or SickoDevZ may rejoin them anonymously to continue updating the CriminalMW. It appears that the recent arrest of SickoDevZ will not halt the development of malware nor bring an end to the CriminalMW Group.
Looking forward, it is clear that the landscape of Android malware targeting financial systems will continue to evolve, with threat actors continuously innovating to evade detection and maximize their illicit gains. Consequently, it is increasingly essential for users to exercise caution when downloading applications and sharing sensitive information in order to mitigate these risks effectively.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Only install software from official app stores such as the Play Store or the iOS App Store.
- Using a reputed antivirus and internet security software package is recommended on connected devices, including PCs, laptops, and mobile.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Be careful while opening links received via SMS or emails sent to your mobile device.
- Google Play Protect should always be enabled on Android devices.
- Be wary of any permissions that you give an application.
- Keep devices, operating systems, and applications up to date.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware distribution via phishing site |
| Persistence (TA0028) | Event Triggered Execution: Broadcast Receivers (T1624.001) | The malware registered broadcast receivers to trigger malicious actions. |
| Defense Evasion (TA0030) | Hide Artifacts: Suppress Application Icon (T1628.001) | Hide icons based on the command received from the server |
| Defense Evasion (TA0030) | Hide Artifacts: User Evasion (T1628.002) | Silents the device while executing ATS |
| Defense Evasion (TA0030) | Impair Defenses: Prevent Application Removal (T1629.001) | Prevent uninstallation |
| Defense Evasion (TA0030) | Indicator Removal on Host: Uninstall Malicious Application (T1630.001) | CriminalMW can uninstall itself |
| Defense Evasion (TA0030) | Virtualization/Sandbox Evasion: System Checks (T1633.001) | Malware implemented anti-emulation check using a third-party library |
| Defense Evasion (TA0030) | Input Injection (T1516) | Malware can mimic user interaction, perform clicks and various gestures, and input data |
| Discovery (TA0032) | Software Discovery (T1418) | Collects installed application details |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) | Steals SMSs from the infected device |
| Collection (TA0035) | Call Control (T1616) | CriminalMW can make calls without the user’s knowledge |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 152b3cda192f092160c2f4eaa6d696d20f63cf27e3b479328d2f392891dce87a 98358b77e01e11d024c618d129701546f1af1c14 30b7d1c865335266979e96f8ddbfb708 | SHA256 SHA1 MD5 | Malicious APK file hash |
| Criminalmw[.]fun | Domain | Criminal bot domain |
| 5dbea04fa976dfdc36d3303aa627e5be71ddc7bf114818a300d3f454d8315ce9 90c7e739e6f06204d59c9b2cff217d4140a457f3 de866b01d1b965a8b6423ab7c2ff2885 | SHA256 SHA1 MD5 | Phishing site |
| 03ae540c1b1eb419bc3607deb9abd378d7ba8df41b407e10b307ffee0616e7c4 e65e16bddfb024ed866485e93d4a52eed61e744e db47978be15209894180454f993ffbe6 | SHA256 SHA1 MD5 | Malware download URL |
| 2c7a1ad11469abe84cb7e378d814b79a3339bfcf1ccc598ea651ec0ab24bb3e0 032f679714248bc5681bd409df0ec1465f5d0e9d 30f1be8974e018e6b293fe5de9515bcc | SHA256 SHA1 MD5 | Malicious APK file hash |
| 450d0e64814abffc854f3f55a2faffbbf8a1c13c8b8b67ac03f4e2bc85ec0d23 950117f9ce18402a7072afc5593c667420141339 e827f0fb88ba829edd5050bdcc7fd5b0 | SHA256 SHA1 MD5 | Malicious APK file hash |
| 592d9fc0234f437972da1cc1cd20cb20a478b2ad7d07d0ded902a15ca94f2ade b4ab19d073644fb2a5f8b6123bedcb4385647c3c 46a32cb1cabc99875143ca236f88d40e | SHA256 SHA1 MD5 | Malware download URL |
| 2c354c891d3f24695943c50f866b400dad4e6bc18d1cc5cf1580b368ce859f48 78415a24fe1bb9aa16761798274b196eebdf66d6 d76dfc06a900d16db6ece278c6bec872 | SHA256 SHA1 MD5 | Malicious APK file hash |
| hxxps://playstoreapp[.]fun/apps/app1702152151538.apk | URL | Criminal Bot download URL |
| droidweb[.]net | Domain | Webdroid domain |
Related
如有侵权请联系:admin#unsafe.sh