这是一篇2022年5月的入侵案例,攻击者通过联络表单钓鱼的方式邮递BumbleBee恶意软件成功突破网络边界。我们之前已经披露过2个有关BumbleBee的案例(1, 2),本篇报告与前两篇案例皆在分析利用BumbleBee恶意软件进行后渗透的技战术,
攻击者最初投递一个包含lnk快捷方式+DLL隐藏文件的ISO文件。成功触发DLL文件执行后BumbleBee恶意软件加载了Meterpreter和Cobalt Strike的payload。随后攻击者对内网进行探测、使用两种不同的UAC绕过技术、窃取凭证、利用ZeroLogon漏洞提权并在内网中进行横向移动。
一旦用户点击了下载链接,就会从谷歌的云存储站点storage.googleapis.com下载一个zip压缩包。受害者解压后将会得到一个ISO镜像文件。ISO镜像文件中包含LNK快捷方式文件和一个DLL文件。当用户双击LNK文件后就会调用rundll32.exe加载BumbleBee的恶意DLL文件,起初DLL进程只是外连BumbleBee的C2服务器,但并没有进行其他的活动。
大概过了12个小时,WmiPrivse.exe启动了ImagingDevices.exe并将Meterpreter注入了这个进程。这种行为与我们此前发布的案例类似。该进程也使用了nltest,net,tasklist和whoami进行基础信息收集,又过了37分钟,攻击者将Meterpreter迁移到svchost.exe进程中,并利用UAC绕过技术启动了一个二进制的Meterpreter程序。
攻击者先是用 WSReset 技术和slui hijacking 技术多次尝试绕过UAC失败后,最终还是通过WSReset技术成功绕过UAC,通过Meterpreter的getsystem提权成功。利用SYSTEM权限加载了一个Cobalt Strike的DLL文件。
Cobalt Strike进程开始了第二波信息收集,窃取系统凭证、运行AdFind、nltest、net和systeminfo。攻击者在跳板机中上传了Sysinternals系列中的知名工具ProcDump64并转出了LSASS进程内存。然后又通过reg.exe将SAM、Security和Software三个注册表导出备份。攻击者利用SMB共享,在其他终端的C$\\ProgramData\目录下上传Cobalt Strike的DLL文件,通过远程服务加载DLL文件进行横向移动。虽然攻击者并发了很多链接其他终端的网络连接,但他们依然在跳板机上执行着其他的攻击活动。
攻击活动停止了3小时,又在攻击开始后的第19个小时继续。攻击者开始利用Zerologon(CVE 2020 1472)漏洞成功获取了域控服务器权限。然后攻击者开始使用域管理员组中的一个账号开始PTH攻击。
在跳板机上,攻击者运行了Invoke-Sharefinder并将执行结果保存在本地磁盘中。在另外一台域控服务器中上传了Cobalt Strike DLL并以系统服务的方式加载。
此后攻击者被发现并被踢出网络,基于一台域控服务器被破坏导致网络中的身份认证受到影响,并且攻击者的活动属于投递勒索软件前期技战术活动,我们评估此次入侵为中等风险。
由@0xtornado, @samaritan_o, @RoxpinTeddy分析整理。
本次攻击起始于一个谷歌所属的域名链接——storage.googleapis.com。利用这种白域名进行攻击不仅在邮件账号劫持批量钓鱼中出现,同样在联系表单钓鱼中也很常见。我们评估这种伪装成法律团队网站进行钓鱼,诱导用户下载并打开文件的攻击为中等偏高风险。
用户点击链接后,最终会进入乍一看似乎是合法的谷歌下载站点。
紧接着,用户下载到了一个zip压缩包,解压后得到一个名为StolenImages_Evidence.iso的镜像文件,双击后会自动挂载镜像文件,可以看到一个伪装成正常文件夹的快捷方式。
双击这个快捷方式会执行加载恶意DLL的命令如下:
%windir%\system32\cmd.exe /c start rundll32.exe mkl2n.dll,kXlNkCKgFC利用Eric Zimmerman开发的工具 LECmd,我们注意到这个快捷方式的创建信息与此前披露的入侵案例如出一辙。
快捷方式的属性中可以看到创建者的计算机名、MAC地址以及其他信息:
Machine ID: desktop-30fdj39Mac:eb:33:6a:3b:d0:e3Creation: 2022-02-11 21:22:11
攻击者投递了多个payload以连接到不同的C2服务器,下面的图可以较为直观地展示攻击者如何利用进程注入或投递新的可执行文件连接C2服务器。攻击者使用了Meterpreter和Cobalt Strike两种C2工具。
与之前的BumbleBee案例一致,攻击者选择注入到合法的Windows进程中:
C:\Program Files\Windows Photo Viewer\ImagingDevices.exe派生新进程的手法依然是使用WmiPrvSE.exe
攻击者在跳板机中使用getsystem 模块进行了提权
cmd.exe /c echo wafrms > \\.\pipe\wafrmsC:\Windows\system32\cmd.exe /c echo dec8f35bcbf > \\.\pipe\7fd13a
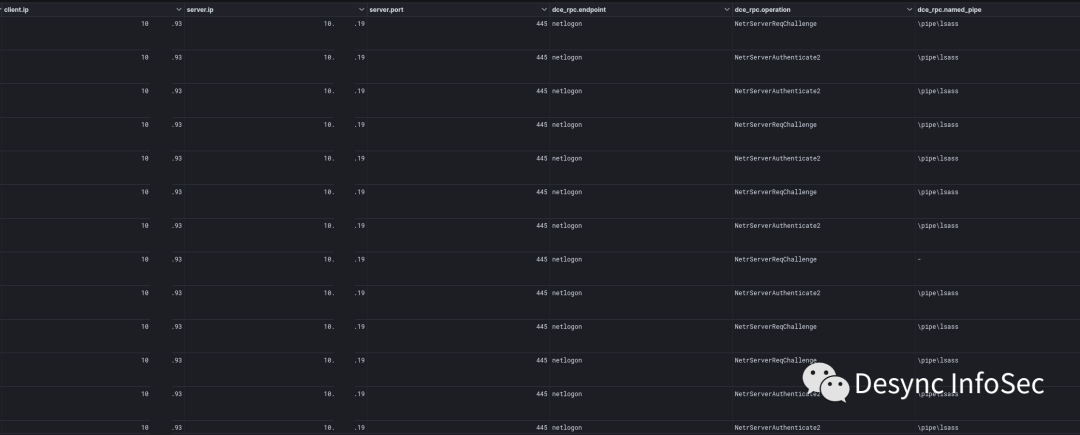
第二天,从跳板机到域控服务器的登录行为激增
这些到域控服务器的连接由各种网络登录请求(NetrServerReqChallenge, NetrServerAuthenticate2, NetrServerPasswordSet2) 组成
在网络侧发现攻击者使用CVE 2020 1472,漏洞(也称ZeroLogon)攻击域控服务器,从Pcap包中我们可以看到漏洞利用成功将凭据重置为全零的数据包。
在域控服务器上会同时生成跳板机修改域控密码事件ID为4742的日志,日志时间与网络侧时间一致。
拿下域控服务器,攻击者开始使用域管理员账号进行PTH攻击。
ImagingDevices.exe通过调用NtAllocateVirtual
MemoryRemoteApiCall执行“svchost.exe
-k UnistackSvcGroup -s WpnUserService”进行进程注入,通过进程内存扫描可以看到其他进程被注入恶意代码的情况:
PID | 进程名称 | 命令行 | .Rule |
576 | winlogon.exe | winlogon.exe | win_cobalt_strike_auto |
836 | svchost.exe | C:\Windows\system32\svchost.exe -k DcomLaunch -p | win_cobalt_strike_auto |
616 | winlogon.exe | winlogon.exe | win_cobalt_strike_auto |
1132 | svchost.exe | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s NcbService | win_cobalt_strike_auto |
6876 | svchost.exe | C:\Windows\system32\svchost.exe -k UnistackSvcGroup | win_cobalt_strike_auto |
9828 | svchost.exe | C:\Windows\system32\svchost.exe -k UnistackSvcGroup | win_cobalt_strike_auto |
攻击者使用WSReset技术和DelegateExecute技术绕过UAC限制使用高权限执行恶意二进制文件
攻击者绕过UAC的过程看上去并非一帆风顺,他们多次尝试绕过失败,结束父进程并重新尝试绕过UAC。
除了WSReset技术,攻击者还尝试了利用Meterpreter集成的slui.exe技术绕过UAC
我们观察到攻击者删除了一些跳板机中的攻击工具
整个入侵过程中,Cobalt Strike进程创建了许多命名管道用于进程间通信,这些命名管道都使用了Cobalt Strike已知的名称。
已知的Cobalt Strike命名管道名称:
\postex_002d\postex_67cc\postex_731d\postex_a4c1\postex_c69e\postex_b6fd\postex_5a0d\postex_d43a\postex_a820
同时我们也发现ImagingDevices.exe在注入Meterpreter时使用的不常用命名管道名称
\4ae13d6c2cd672ae\pipe\spoolss\0029482318be6784\uwjjqz\vllyad
攻击者使用Sysinternals 工具集中的procdump64.exe工具转储LSASS进程,命令如下:
procdump64.exe -accepteula -ma lsass.exe C:\ProgramData\lsass.dmp攻击者使用注入到svchost.exe进程中的Cobalt Strike远程执行Windows自带系统命令reg.exe,导出了注册表中的SAM、SECURYTI和SYSTEM数据。命令如下:
C:\Windows\system32\cmd.exe /C reg.exe save hklm\sam c:\ProgramData\sam.hiveC:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe /C reg.exe save hklm\security c:\ProgramData\security.saveC:\Windows\system32\cmd.exe /C reg.exe save hklm\security c:\ProgramData\security.saveC:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe /C reg.exe save hklm\system c:\ProgramData\system.saveC:\Windows\system32\cmd.exe /C reg.exe save hklm\system c:\ProgramData\system.save
内网探测活动中,攻击者不仅使用Windows自带命令,也使用了像AdFind和PowerSploit的工具。在跳板机中获取到LSASS中的凭证后,攻击者开始对域用户和域内主机进行探测。
af.exe -f "(objectcategory=person)" > ad_users.txtaf.exe -f "objectcategory=computer" > ad_computers.txt
攻击者使用Windows自带命令进行信息收集
nltest /dclist:DOMAINnet view /allnet group "Domain Computers" /domainnet group "domain Admins" /domainwhoamiwhoami /groupsecho %USERDOMAIN%ping -n 1 DOMAINCONTROLLERsysteminfotasklist
攻击者尝试浏览名为sh.txt的文件,该文件保存了Invoke-ShareFinder命令的执行结果,这一行为记录在PowerShell执行日志中,事件id为4103和4104.
Invoke-ShareFinder是PowerSploit攻击框架中的一个模块。用于发现域中开启文件共享的主机。
在跳板机中完成信息收集后,攻击者利用SMB协议进行横向移动,将Cobalt Strike恶意DLL文件复制到目标主机的C:\ProgramData目录下,并以新建系统服务的形式启动。
在被攻击主机的日志中可以观潮到事件id 7045记录了这一行为。
cmd.exe /c rundll32.exe C:\ProgramData\n23.dll,AddProgram整个攻击过程中,攻击者使用了多个C2服务器。
45.153.243.93:443JA3: 0c9457ab6f0d6a14fc8a3d1d149547fbJA3s: 61be9ce3d068c08ff99a857f62352f9dsubject: C=AU, ST=Some-State, O=Internet Widgits Pty Ltdtls.issuerdn : C=AU, ST=Some-State, O=Internet Widgits Pty Ltdtls.notbefore: May 3, 2022 @ 08:04:39.000tls.notafter: May 3, 2023 @ 08:04:39.000213.232.235.199:443JA3: 0c9457ab6f0d6a14fc8a3d1d149547fbJA3s: 61be9ce3d068c08ff99a857f62352f9dsubject: C=AU, ST=Some-State, O=Internet Widgits Pty Ltdtls.issuerdn : C=AU, ST=Some-State, O=Internet Widgits Pty Ltdtls.notbefore: May 2, 2022 @ 19:09:22.000tls.notafter: May 2, 2023 @ 19:09:22.000
cevogesu[.]com at 172.93.201.12:443JA3: a0e9f5d64349fb13191bc781f81f42e1JA3s: ae4edc6faf64d08308082ad26be60767subject: CN=titojukus.comtls.issuerdn: C=GB, ST=Greater Manchester, L=Salford, O=Sectigo Limited, CN=Sectigo RSA Domain Validation Secure Server CAtls.notbefore: Apr 22, 2022 @ 00:00:00.000tls.notafter: Apr 22, 2023 @ 23:59:59.000titojukus[.]com at 23.106.215.100:443JA3: a0e9f5d64349fb13191bc781f81f42e1JA3s: ae4edc6faf64d08308082ad26be60767subject: CN=titojukus.comtls.issuerdn: C=GB, ST=Greater Manchester, L=Salford, O=Sectigo Limited, CN=Sectigo RSA Domain Validation Secure Server CAtls.notbefore: Apr 22, 2022 @ 00:00:00.000tls.notafter: Apr 22, 2023 @ 23:59:59.000
{"x64": {"sha1": "fa9597b87f78c667cc006aaa1c647d539aa9b827","md5": "ea2c1fa8668812852a77737c4f712ba2","config": {"C2 Server": "cevogesu.com,/eo.html,titojukus.com,/eo.html","Polling": 5000,"C2 Host Header": "","HTTP Method Path 2": "/fam_newspaper","Watermark": 1580103814,"Method 1": "GET","Spawn To x64": "%windir%\\sysnative\\rundll32.exe","Jitter": 23,"Spawn To x86": "%windir%\\syswow64\\rundll32.exe","Method 2": "POST","Port": 443,"Beacon Type": "8 (HTTPS)"},"sha256": "da3c4e2b7768d66ecb6c0e74c6d45e2bcfbc6203b76c7163909bd2061603cef5","time": 1651717062232.1,"uri_queried": "/DhpA"},"x86": {"sha1": "785b660537506501e695e46875b02260649b23f7","md5": "5d2a8724dbce65eefb7e74fbb0eceda9","config": {"C2 Server": "cevogesu.com,/cs.html,titojukus.com,/cs.html","Polling": 5000,"C2 Host Header": "","HTTP Method Path 2": "/posting","Watermark": 1580103814,"Method 1": "GET","Spawn To x64": "%windir%\\sysnative\\rundll32.exe","Jitter": 23,"Spawn To x86": "%windir%\\syswow64\\rundll32.exe","Method 2": "POST","Port": 443,"Beacon Type": "8 (HTTPS)"},"sha256": "f7bfde050c81d47d79febdb170f307f447e76253715859727beff889d2a91694","time": 1651717054821.8,"uri_queried": "/BiLe"}}
ec2-3-16-159-37.us-east-2.compute.amazonaws[.]com at 3.16.159.37:80/443JA3: ce5f3254611a8c095a3d821d44539877, a0e9f5d64349fb13191bc781f81f42e1JA3s: ec74a5c51106f0419184d0dd08fb05bcsubject: C=US, ST=DE, O=Hackett LLC, OU=calculate, CN=hackett.llc.com, [email protected]tls.issuerdn: C=US, ST=DE, O=Hackett LLC, OU=calculate, CN=hackett.llc.com, [email protected]tls.ja3.hashtls.notbefore: Sep 13, 2020 @ 21:43:47.000tls.notafter: Sep 12, 2027 @ 21:43:47.000
在获取域控服务器权限后,攻击者尝试执行了一些操作,随后被踢出网络。应急响应期间发现主域控服务器由于收到攻击,整个域的身份认证都无法正常进行。
BumbleBee C245.153.243.93:443213.232.235.199:443CobaltStrikecevogesu[.]com at 172.93.201.12:443titojukus[.]com at 23.106.215.100:443Meterpreterec2-3-16-159-37.us-east-2.compute.amazonaws[.]com at 3.16.159.37:80 and 3.16.159.37:44
documents.lnkEE7AD5FE821FB9081380DBBF40C4F06238EEF0CDAA8FAA27C9E2CEDEAFCFE842E2E0E08E3C600328E1085DC73D672D068F3056E79E66BEC7020BE6AE907DD541201CD167mkl2n.dllAEFF99611BABD41D79C3BA7930F00BC1FA3649B0472BA7FD9B31A22C904B2DE4C008F540F7C1D064B95DC0B76C44764CD3AE7AEB21DD5B161E5D218E8D6E0A7107D869C1n23.dllB3E68AEBE05DC652EC65099E0E98B94E52D4C0CB9A93E7BC5F1E0C386DCCA3E0AC41B96665A9B1BCDE2C518BC25DD9A56FD13411558E7F24BBDBB8CB92106ABBC5463ECFStolenImages_Evidence.isoFBCAA31456F39F996950511705461639759688D1245AACD0ED067B0F0388786E911AAF284BB67453A441F48C75D41F7DC56F8D58549AE94E7AEAB48A7FFEC8B78039E5CCwSaAHJzLLT.exeBD5C8EA8C231BF2775B9C0BA3F7EA867CCC9E1559B877B04B1D0E7F8920A64B4E35136DADF63149EEC96575D66D90DA697A50B7C47C3D7637E18D4DF1C24155ABACBC12
检测特征方面
整个攻击过程会触发以下Suricata IDS规则:
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O)ET POLICY SMB2 NT Create AndX Request For a DLL File - Possible Lateral MovementET RPC DCERPC SVCCTL - Remote Service Control Manager AccessET POLICY SMB Executable File TransferET SCAN Behavioral Unusual Port 445 traffic Potential Scan or Infection
Sigma
Abused Debug Privilege by Arbitrary Parent Processes
AdFind Usage Detection
Bypass UAC Using DelegateExecute
Bypass UAC via WSReset.exe
UAC Bypass WSReset
Cobalt Strike Named Pipe
Correct Execution of Nltest.exe
Cred Dump Tools Dropped Files
LSASS Memory Access by Tool Named Dump
LSASS Memory Dumping
Malicious PowerView PowerShell Commandlets
Meterpreter or Cobalt Strike Getsystem Service Installation
Meterpreter or Cobalt Strike Getsystem Service Start
Mimikatz Detection LSASS Access
Registry Dump of SAM Creds and Secrets
Shell Open Registry Keys Manipulation
Successful Overpass the Hash Attempt
Suspicious PowerShell Invocations – Specific
Suspicious PowerShell Keywords
Suspicious Rundll32 Without Any CommandLine Params
Suspicious Service Installation
Suspicious Use of Procdump
Suspicious Use of Procdump on LSASS
Yara
/*YARA Rule SetAuthor: The DFIR ReportDate: 2022-11-13Identifier: Case 13842 BumblebeeReference: https://thedfirreport.com/*//* Rule Set ----------------------------------------------------------------- */rule bumblebee_13842_documents_lnk {meta:description = "BumbleBee - file documents.lnk"author = "The DFIR Report via yarGen Rule Generator"reference = "https://thedfirreport.com"date = "2022-11-13"hash1 = "3c600328e1085dc73d672d068f3056e79e66bec7020be6ae907dd541201cd167"strings:$x1 = "$..\\..\\..\\..\\Windows\\System32\\cmd.exe*/c start rundll32.exe mkl2n.dll,kXlNkCKgFC\"%systemroot%\\system32\\imageres.dll" fullword wide$x2 = "C:\\Windows\\System32\\cmd.exe" fullword ascii$x3 = "%windir%\\system32\\cmd.exe" fullword ascii$x4 = "Gcmd.exe" fullword wide$s5 = "desktop-30fdj39" fullword asciicondition:uint16(0) == 0x004c and filesize < 4KB and1 of ($x*) and all of them}rule bumblebee_13842_StolenImages_Evidence_iso {meta:description = "BumbleBee - file StolenImages_Evidence.iso"author = "The DFIR Report via yarGen Rule Generator"reference = "https://thedfirreport.com"date = "2022-11-13"hash1 = "4bb67453a441f48c75d41f7dc56f8d58549ae94e7aeab48a7ffec8b78039e5cc"strings:$x1 = "$..\\..\\..\\..\\Windows\\System32\\cmd.exe*/c start rundll32.exe mkl2n.dll,kXlNkCKgFC\"%systemroot%\\system32\\imageres.dll" fullword wide$x2 = "C:\\Windows\\System32\\cmd.exe" fullword ascii$x3 = "%windir%\\system32\\cmd.exe" fullword ascii$x4 = "Gcmd.exe" fullword wide$s5 = "pxjjqif723uf35.dll" fullword ascii$s6 = "tenant unanimously delighted sail databases princess bicyclelist progress accused urge your science certainty dalton databases h" ascii$s7 = "mkl2n.dll" fullword wide$s8 = "JEFKKDJJKHFJ" fullword ascii /* base64 encoded string '$AJ(2I(qI' */$s9 = "KFFJJEJKJK" fullword ascii /* base64 encoded string '(QI$BJ$' */$s10 = "JHJGKDFEG" fullword ascii /* base64 encoded string '$rF(1D' */$s11 = "IDJIIDFHE" fullword ascii /* base64 encoded string ' 2H 1G' */$s12 = "JHJFIHJJI" fullword ascii /* base64 encoded string '$rE rI' */$s13 = "EKGJKKEFHKFFE" fullword ascii /* base64 encoded string '(bJ(AG(QD' */$s14 = "FJGJFKGFF" fullword ascii /* base64 encoded string '$bE(aE' */$s15 = "IFFKJGJFK" fullword ascii /* base64 encoded string ' QJ$bE' */$s16 = "FKFJDIHJF" fullword ascii /* base64 encoded string '(RC rE' */$s17 = "EKFJFdHFG" fullword ascii /* base64 encoded string '(REtqF' */$s18 = "HJFJJdEdEIDK" fullword ascii /* base64 encoded string '$RItGD 2' */$s19 = "KFJHKDJdIGF" fullword ascii /* base64 encoded string '(RG(2] a' */$s20 = "documents.lnk" fullword widecondition:uint16(0) == 0x0000 and filesize < 13000KB and1 of ($x*) and 4 of them}rule bumblebee_13842_mkl2n_dll {meta:description = "BumbleBee - file mkl2n.dll"author = "The DFIR Report via yarGen Rule Generator"reference = "https://thedfirreport.com"date = "2022-11-13"hash1 = "f7c1d064b95dc0b76c44764cd3ae7aeb21dd5b161e5d218e8d6e0a7107d869c1"strings:$s1 = "pxjjqif723uf35.dll" fullword ascii$s2 = "tenant unanimously delighted sail databases princess bicyclelist progress accused urge your science certainty dalton databases h" ascii$s3 = "JEFKKDJJKHFJ" fullword ascii /* base64 encoded string '$AJ(2I(qI' */$s4 = "KFFJJEJKJK" fullword ascii /* base64 encoded string '(QI$BJ$' */$s5 = "JHJGKDFEG" fullword ascii /* base64 encoded string '$rF(1D' */$s6 = "IDJIIDFHE" fullword ascii /* base64 encoded string ' 2H 1G' */$s7 = "JHJFIHJJI" fullword ascii /* base64 encoded string '$rE rI' */$s8 = "EKGJKKEFHKFFE" fullword ascii /* base64 encoded string '(bJ(AG(QD' */$s9 = "FJGJFKGFF" fullword ascii /* base64 encoded string '$bE(aE' */$s10 = "IFFKJGJFK" fullword ascii /* base64 encoded string ' QJ$bE' */$s11 = "FKFJDIHJF" fullword ascii /* base64 encoded string '(RC rE' */$s12 = "EKFJFdHFG" fullword ascii /* base64 encoded string '(REtqF' */$s13 = "HJFJJdEdEIDK" fullword ascii /* base64 encoded string '$RItGD 2' */$s14 = "KFJHKDJdIGF" fullword ascii /* base64 encoded string '(RG(2] a' */$s15 = "magination provided sleeve governor earth brief favourite setting trousers phone calamity ported silas concede appearance abate " ascii$s16 = "wK}zxspyuvqswyK" fullword ascii$s17 = "stpKspyq~sqJvvvJ" fullword ascii$s18 = "ntribute popped monks much number practiced dirty con mid nurse variable road unwelcome rear jeer addition distract surgeon fall" ascii$s19 = "uvzrquxrrwxur" fullword ascii$s20 = "vvvxvsqrs" fullword asciicondition:uint16(0) == 0x5a4d and filesize < 9000KB and8 of them}rule bumblebee_13842_n23_dll {meta:description = "BumbleBee - file n23.dll"author = "The DFIR Report via yarGen Rule Generator"reference = "https://thedfirreport.com"date = "2022-11-13"hash1 = "65a9b1bcde2c518bc25dd9a56fd13411558e7f24bbdbb8cb92106abbc5463ecf"strings:$x1 = "scratched echo billion ornament transportation heedless should sandwiches hypothesis medicine strict thus sincere fight nourishm" ascii$s2 = "omu164ta8.dll" fullword ascii$s3 = "eadlight hours reins straightforward comfortable greeting notebook production nearby rung oven plus applet ending snapped enquir" ascii$s4 = "board blank convinced scuba mean alive perry character headquarters comma diana ornament workshop hot duty victorious bye expres" ascii$s5 = " compared opponent pile sky entitled balance valuable list ay duster tyre bitterly margaret resort valuer get conservative contr" ascii$s6 = "ivance pay clergyman she sleepy investigation used madame rock logic suffocate pull stated comparatively rowing abode enclosed h" ascii$s7 = " purple salvation dudley gaze requirement headline defective waiter inherent frightful night diary slang laurie bugs kazan annou" ascii$s8 = "nced apparently determined among come invited be goodwill tally crowded chances selfish duchess reel five peaceful offer spirits" ascii$s9 = "scratched echo billion ornament transportation heedless should sandwiches hypothesis medicine strict thus sincere fight nourishm" ascii$s10 = "s certificate breeze temporary according peach effected excuse preceding reaction channel bring short beams scheme gosh endless " ascii$s11 = "rtificial poke reassure diploma potentially " fullword ascii$s12 = "led spree confer belly rejection glide speaker wren do create evenings according cultivation concentration overcoat presume feed" ascii$s13 = "EgEEddEfhkdddEdfkEeddjgjehdjidhkdkeiekEeggdijhjidgkfigEgggdjkhkjkedEigifefdfhEjgghgEhjkeihifdhEEdgifefgkkEfEijhkhkhidddEdhgidfkE" ascii$s14 = "kgfjjjEEgkdiehfeEjihkfEeididdeEjhggEjedhdfEjiddgEgghejEidEfEEfgfjfhdghfddfihfidfEedikfdfjkiffkjiijiiijdhgghekhkegkidkgfjijhkiigg" ascii$s15 = "eekgEeideheghidkkEkkfkjikhiEhiefggdkhifdgEhhdEkkEkgjdEjjeEjhjhihfdgEdEidigefhhikdgdfEEdjEeggiEdfkdEdiEffdddkgikhhkihigEhjEdehieh" ascii$s16 = "eddEfefEEd" ascii$s17 = "hiefgfgkdfhgEdhEEgfhfegiiekgkdheihfjjhdeediefEkekdgeihhdfhhgjjiddjehgEhigEkEiEghejfidgjkdjidfkkfjEkfidfdiihkkEdEkEjjkEghfEdiihgE" ascii$s18 = "kfifkfkgdgdfhefdfejjdjigEhghidiiEekeEidEhghijgfkgkkedeeiggeEdhddkdhgigdjEihjiEjkgjjEefedfhidjkEjfghfjfdfdEjhkjjddjEfdgkEEikifdhE" ascii$s19 = "dedkdeeeeefgdEgfkkiEEfidikkffgighgEfiEEidgehdeiEhhjhjgiEdfkjihEgdgdefgkEfigdfedijhejEgdhkEdifEehifgdhddhfjghjfiifdhiigedggEdikeE" ascii$s20 = "efigfkfkkkfkdifiEhkhjkiejjidgkEfhEfehidhEfekgejgefEjEgdgefgidjjfdkjEfgfEigijhidideEEffjefkkkjjeeigggiighdddEddgegjEfEffjjjiddiEk" asciicondition:uint16(0) == 0x5a4d and filesize < 200KB and1 of ($x*) and 4 of them}rule bumblebee_13842_wSaAHJzLLT_exe {meta:description = "BumbleBee - file wSaAHJzLLT.exe"author = "The DFIR Report via yarGen Rule Generator"reference = "https://thedfirreport.com"date = "2022-11-13"hash1 = "df63149eec96575d66d90da697a50b7c47c3d7637e18d4df1c24155abacbc12e"strings:$s1 = "ec2-3-16-159-37.us-east-2.compute.amazonaws.com" fullword ascii$s2 = "PAYLOAD:" fullword ascii$s3 = "AQAPRQVH1" fullword ascii$s4 = "AX^YZAXAYAZH" fullword ascii$s5 = "/bIQRfeCGXT2vja6Pzf8uZAWzlUMGzUHDk" fullword ascii$s6 = "SZAXM1" fullword ascii$s7 = "[email protected]" fullword ascii$s8 = "@.nbxi" fullword ascii$s9 = "Rich}E" fullword asciicondition:uint16(0) == 0x5a4d and filesize < 20KB andall of them}
Att&ck映射
Malicious File – T1204.002Windows Command Shell – T1059.003PowerShell – T1059.001Process Injection – T1055File Deletion – T1070.004LSASS Memory – T1003.001Exploitation for Privilege Escalation – T1068Lateral Tool Transfer – T1570Valid Accounts – T1078Service Execution – T1569.002SMB/Windows Admin Shares – T1021.002Remote System Discovery – T1018Process Discovery – T1057Domain Groups – T1069.002Rundll32 – T1218.011Domain Account – T1087.002System Information Discovery – T1082Security Account Manager – T1003.002Network Share Discovery – T1135Pass the Hash – T1550.002Mark-of-the-Web Bypass – T1553.005Bypass User Account Control – T1548.002Web Protocols – T1071.001Spearphishing Link – T1566.002Masquerading – T1036
如有侵权请联系:admin#unsafe.sh