
CSRB Microsoft Review

The Cyber Safety Review Board (CSRB) published their findings from their investigation into the Microsoft cloud compromise last year. The intrusion led to the compromise of the email accounts of many people, including senior U.S. government officials. So I suppose it is no surprise that the CSRB wanted to investigate.
The findings are a fairly scathing indictment of security at Microsoft, highlighting a series of failures that exacerbated the severity of the problems. I’m not going to dive into the individual findings, but I recommend reviewing the report. Even if you only review the executive summary.
I am somewhat excited to see the CSRB produce this report, I think there is value in this sort of third party investigation following breaches. I think it is important as an industry that we start to operate not just under the auspices of “security,” but of “safety.” I think there is a subtle difference that is worth further exploring, perhaps in a future essay or conference talk. In the meantime, I thing Security Chaos Engineering is a phenomenal book that touches on some of the things that I think ultimately contribue to thinking of systems in terms of safety.
Device Bound Session Cookies
This week, the Chromium blog published a post about work being done to curb the risks of cookie theft through the introduction of device bound session cookies.
Cookie theft remains a lucrative and powerful attack method that is practically completely unmitigated today. Your company might invest thousands, or even millions of dollars in zero trust solutions, centralized identity management, and hardware security tokens, only to be foiled by the theft of one little string, often between 16 and 32 bytes long.
Browsers have taken a lot of steps to try to prevent cookies from being stolen, but at the end of the day, the browser needs to be able to seemlessly access the cookies. This means that any attempts to secure them can only go so far before they become untenable for users. One of my favorite posts about stealing cookies is “Stealing Chrome cookies without a password”, by the incredible hacker, who goes only by “Alex.”
Device Bound Session Cookies (DBSC) introduces an option for browsers to implement and for site-owners to deploy that enables binding these session cookies to the hardware that they were issued to, via a periodic signing operation with the hardware TPM. Instead of a single cookie that might be valid for days or weeks, implementers will use short-term cookies that are refreshed through a new DBSC-specific process that uses public key cryptography to verify proof of possession.
What this ultimately means is that cookies that are stolen from a site that correctly implements DBSC will only be valid for a short window before becoming invalidated when they are next checked. This will be a huge step forward, as it will force attackers to remain on the device if they want to abuse sessions, and the longer they are on the device, the higher the likelihood that your endpoint security solutions will detect them.
Unfortunately, I anticipate this “solving” cookie theft in much the same way that SPF, DKIM, and DMARC have “solved” email spam. It’ll work great for the sites that implement it, but because it’ll be opt-in and requires server-side support, it’ll have a long tail. At least big sites like Google, Microsoft, Okta, and others will be able to benefit, which will significantly reduce the impacts of session cookie theft. One way that I would love to be proved wrong is if common server software can implement DBSC without applications needing to be aware – if nginx, apache, traefik, etc all could handle the DBSC validation without applications having to care, then I could see this getting much more widespread.
Pwnagotchi
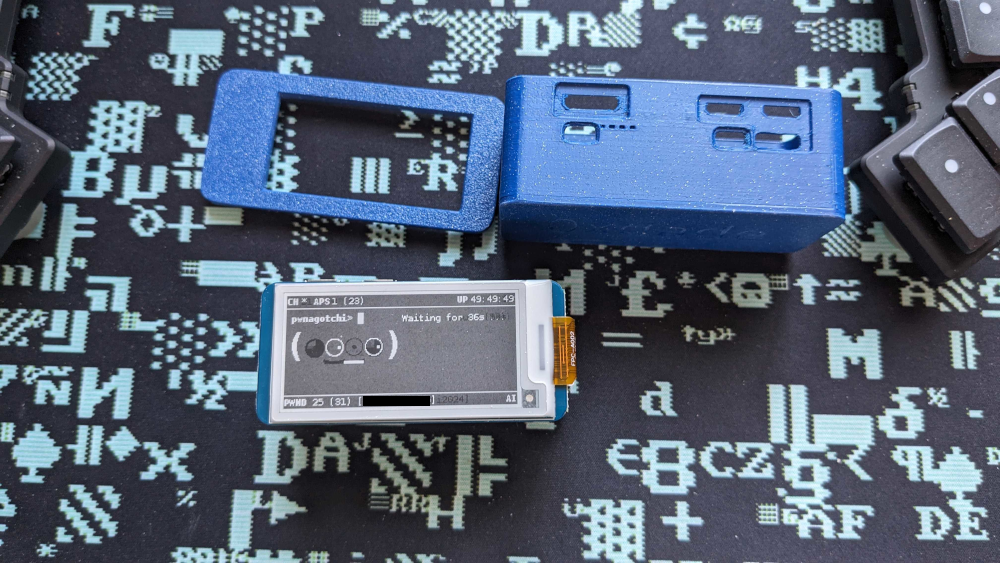
I built a pwnagotchi this week, using an old Raspberry Pi Zero W, a Waveshare V4 e-ink screen, and a PiSugar 3 battery. It was pretty easy to build, but I did need to buy a hammer-in GPIO pin header, since my Pi Zero W didn’t have any GPIO pins.
Everything I needed to get set up:
- My Pi Zero W kit - I bought this back in 2018 and have literally done nothing with it since. $32.99
- 2.13 inch E-Ink WaveShare V4 Screen $20.59
- Pisugar 3 1200 mAh Battery $39.99
- Vilros 40 Pin Hammer-in Pin Header $14.99
- 32GB Samsung EVO Micro SDHC card $11.80
In total, I spent $120.36 on my pwnagotchi project. I also have a slim 3D printed case that phreck printed for me. It’s a bit slimmer than other cases, but requires trimming down the GPIO pins a bit before I can fit it all together.
I ended up struggling a bit with the software side of things. It turns out the “official” site, pwnagotchi.ai, hasn’t been updated in quite some time and the official firmwares don’t support newer hardware. Once I figured out that I should get firmware and information from pwnagotchi.org, it became easier to get functional. Overall it definitely still leaves some room to be improved, as far as documentation goes. But it’s up and running now, and that’s what matters.
Other Personal Updates
I took two days off at the beginning of the week – no work, no work-like activities (e.g. all the development and security projects that I’m interested in). Just… made myself take some time off, for the first time so far in 2024. Turns out, I don’t really know what to do with myself when I’m not working.
I have been keeping it quiet, but I’m working on my own company in the background, which I’ll formally announce in a while. It’s just a part time thing right now, I’m still pretty happy at my day job, but I wanted to start working on something that is mine. I’m working with an artist on branding right now, which I’m very excited about and can’t wait to share.
I also pre-ordered my Framework 16 laptop, naturally I ordered the DIY version. I may have gone a little overboard on it, but I’m very excited for it. I’ve been following Framework since they announced their first laptop, and I am hopeful that they are able to succeed and hopefully change the game for personal electronics going forward.
I’ve been slowly working through Rustlings and The Rust Programming Language, trying to learn why everyone is so excited about Rust. I’m not far into it, only about to start working through chapter 5, but I’m definitely seeing why folks like it.
What I’m Reading

The Internet Con
By Cory Doctorow
ISBN: 978-1-80429-124-5
Learn More
I’m still working on this, I’m about halfway through. I was surprised to learn that many countries created their versions of the DMCA within the last decade or so – it feels insane to see all the things wrong with the DMCA since it’s inception, and then produce similar laws.
Interesting Links
- The Reason I Stopped Using Postman for API Pentests - I used to think Postman was a really cool and useful tool for API testing, but I think their recent moves have diminished this for me.
- Security Risks of Postman - Similar to the previous, this also highlights some of the security risks of using Postman.
- Failure is always an option - A 47 minute conference talk from NDC Copenhagen 2022, by Dylan Beattie. Dylan is a great speaker, and this is one of my favorite talks of his (though it’s hard to pick just one, they are all great).
- Dark Wire - An upcoming book from Joseph Cox, telling the story of an FBI tech startup designed to sell pre-compromised “secure” phones to criminal organizations.
Upcoming Projects
- I am wrapping up the outline for a talk idea that I’d like to submit to BSides Las Vegas. (Due: 2024-04-21)
- I am toying with the idea of submitting a training around docker and dependency management to OWASP Global AppSec. (Due: 2024-05-06)
- I am interested in applying for the Defcon 32 Call for Artist to do a nerdcore show at Defcon this year. I have been putting together a set list and practicing performing in preparation. (Due: 2024-06-01)
- I recently wrapped up recording a new song, “Oh Dade”, produced by Mikal kHill. It still needs to be mixed and some finishing touches added, then I will be submitting it to the Defcon Call for Soundtrack. If it’s accepted, it will debut on the Defcon soundtrack. If it’s not accepted, I will release it the same day I find out it’s not accepted. (Due: 2024-06-01)
如有侵权请联系:admin#unsafe.sh